Running SonarQube With Docker Compose
It’s impossible to overstate the importance of code quality to your project’s success. You can spend enormous amounts of time and money on your agile practice and your CI/CD pipeline, but if your code doesn’t work, you’re not going to get anywhere. Running SonarQube will aim to help developers write code that is better, safer, and more reliable.
In this post, you’ll see how easy it is to integrate SonarQube into your build process. You’ll set up a SonarQube server with Docker and run analysis on a small Java project.
What Is SonarQube?
SonarQube is a code review tool for finding bugs, code smells, and vulnerabilities. It’s available as an open-source platform, but SonarSource also offers enterprise and data center licenses with advanced features.
SonarQube supports a variety of programming languages, including Java, C#, C/C++, JavaScript, TypeScript, COBOL, Apex, PHP, Kotlin, Ruby, Scala, HTML, CSS, ABAP, Flex, Objective-C, Python, Go, Swift, PL/SQL, T-SQL, VB.NET, VB6, and XML. Some languages require a commercial license, though.
You don’t have to change your workflow or learn new tools to use SonarQube. It integrates with common build tools like Ant, Maven, Make, MSBuild, and Gradle. Just add the appropriate plugin, and you can run analysis as part of your regular build process.
Running SonarQube With Docker Compose
You’ll use docker-compose to run SonarQube in Docker with a proper database back end. This compose file sets up SonarQube with PostgreSQL:
version: "3"
services:
sonarqube:
image: sonarqube
restart: unless-stopped
environment:- SONARQUBE_JDBC_USERNAME=sonarqube
- SONARQUBE_JDBC_PASSWORD=sonarpass
- SONARQUBE_JDBC_URL=jdbc:postgresql://db:5432/sonarqube
ports:
- "9000:9000"
- "9092:9092"
volumes:
- sonarqube_conf:/opt/sonarqube/conf
- sonarqube_data:/opt/sonarqube/data
- sonarqube_extensions:/opt/sonarqube/extensions
- sonarqube_bundled-plugins:/opt/sonarqube/lib/bundled-plugins
db:
image: postgres
restart: unless-stopped
environment:- POSTGRES_USER=sonarqube
- POSTGRES_PASSWORD=sonarpass
- POSTGRES_DB=sonarqube
volumes:
- sonarqube_db:/var/lib/postgresql
- postgresql_data:/var/lib/postgresql/data
volumes:
postgresql_data:
sonarqube_bundled-plugins:
sonarqube_conf:
sonarqube_data:
sonarqube_db:
sonarqube_extensions:
The SonarQube section starts on line No. 4. Rather than specifying a version, the compose file uses the latest image.
The environment section defines variables for connecting to the PostgreSQL database.
On line No. 14, it points SonarQube at four volumes for storing configuration. So, this container will store its data between restarts.
Next, the PostgreSQL section uses the latest container, too. It has an environment section that defines variables for SonarQube to log in and the database SonarQube defines in its JDBC connection string.
Finally, it uses two volumes of its own.
Start the containers with docker-compose:
$ sudo docker-compose up -d
Creating network "sonarqube_default" with the default driver
Creating volume "sonarqube_postgresql_data" with default driver
Creating volume "sonarqube_sonarqube_db" with default driver
Creating volume "sonarqube_sonarqube_data" with default driver
Creating volume "sonarqube_sonarqube_bundled-plugins" with default driver
Creating volume "sonarqube_sonarqube_conf" with default driver
Creating volume "sonarqube_sonarqube_extensions" with default driver
Creating sonarqube_db_1 ...
Creating sonarqube_sonarqube_1 ...
Creating sonarqube_db_1
Creating sonarqube_db_1 ... done
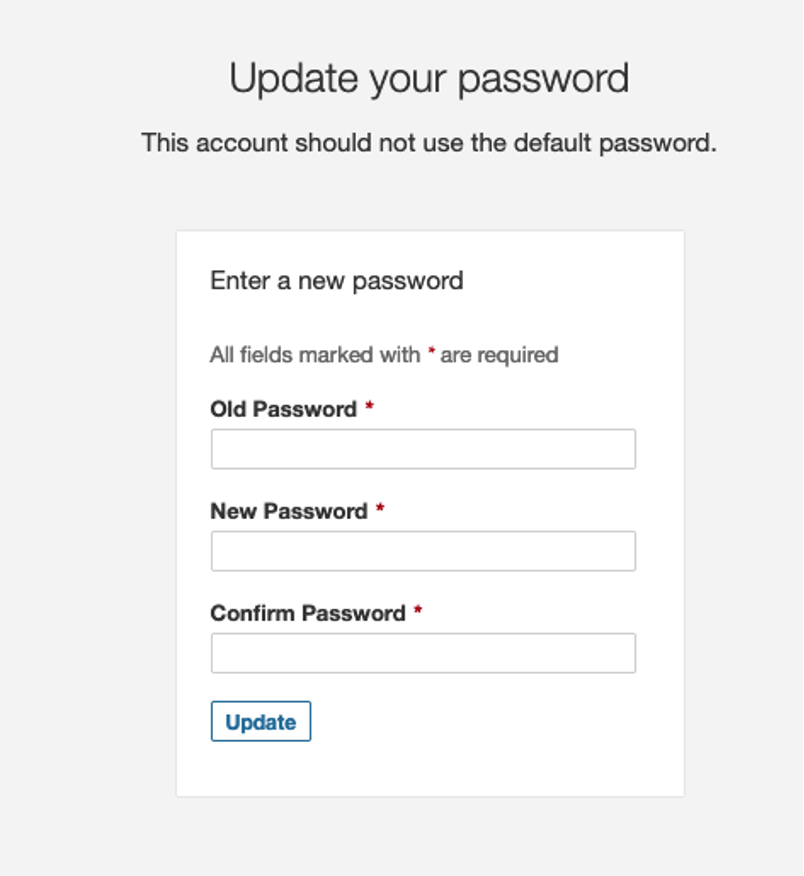
Now, point your browser at http://localhost:9000 and log in with the default admin account with password admin.
You’ll be prompted to change the admin password.
You’re in! You’ve built a SonarQube server. Now, let’s point a Java build at it.
SonarQube and Gradle
SonarSource has sample projects on GitHub. Clone this repo. For this example, you’ll use the sonarqube-scanner-gradle project.
The build.gradle file is already set up for SonarQube.
plugins {
id "jacoco"
id "java"
id "application"
id "org.sonarqube" version "3.0"
}
description = 'Example of SonarQube Scanner for Gradle Usage'
version = '1.0'
sonarqube {
properties {property 'sonar.projectName', 'Example of SonarQube Scanner for Gradle Usage'
}
}
Line No. 5 adds the SonarQube Gradle plugin.
Line No. 8 specifies the SonarQube project name. The server will create this project if it doesn’t exist.
So, all you need to do is pass the address for your server and an authentication token on the build command line.
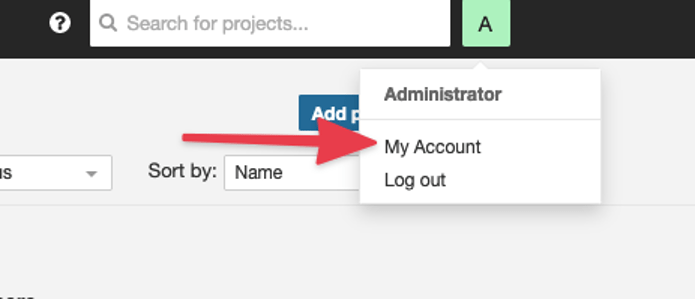
First, create a token.
Go to My Account
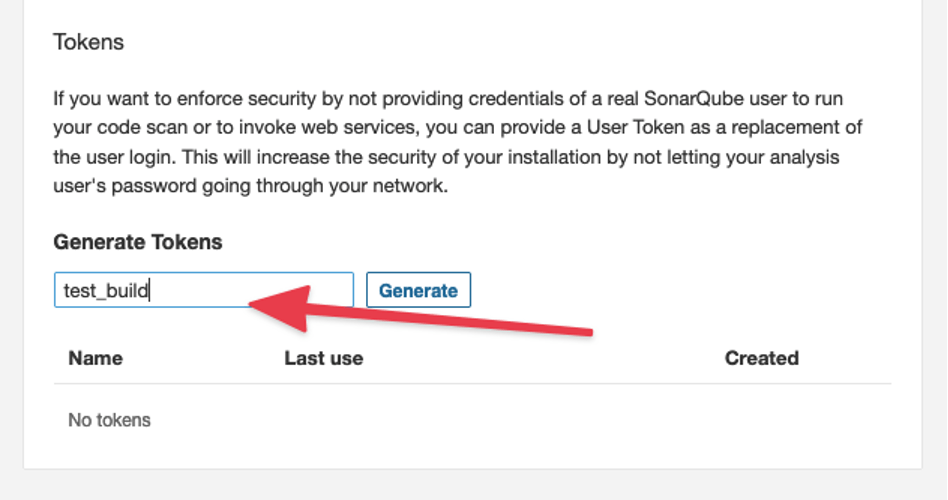
Then, create a token under the security section. Give it a name and click the Generate button.
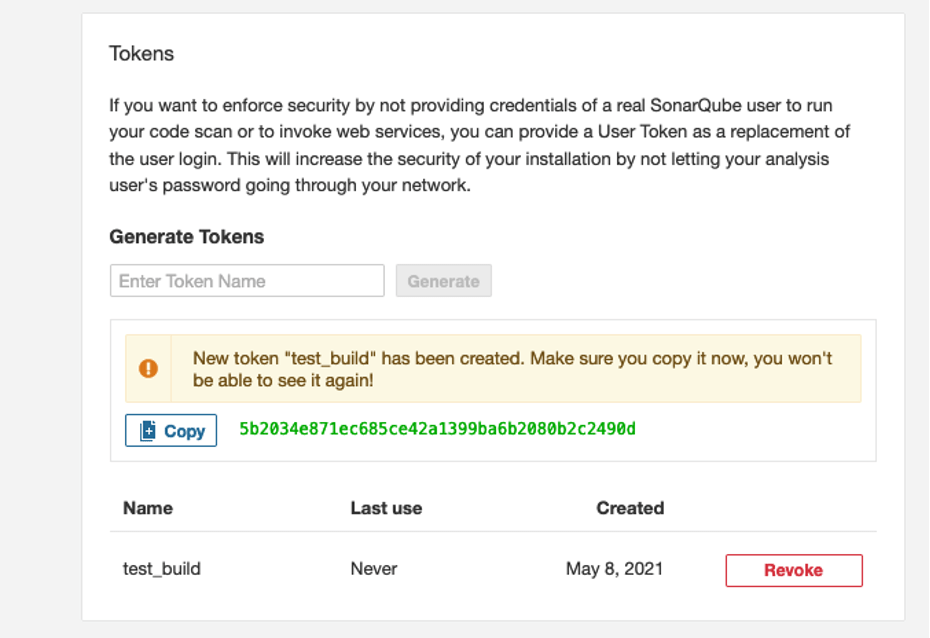
After you click Generate, you’ll see your token. Copy it.
Now, you can run the build. Pass the token with -Dsonar.login and your host with -Dsonar,host.url.
% ./gradlew -Dsonar.login=5b2034e871ec685ce42a1399ba6b2080b2c2490d -Dsonar.host.url=http://myhost:9000 sonarqube BUILD SUCCESSFUL in 15s 3 actionable tasks: 1 executed, 2 up-to-date
Next, check your SonarQube console for build results.
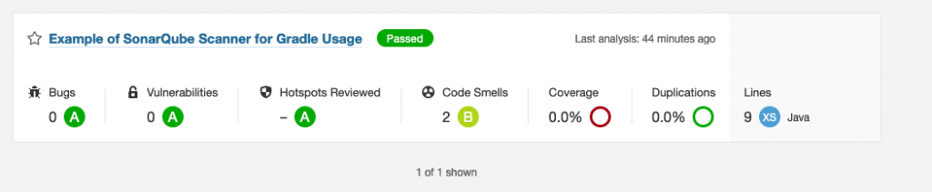
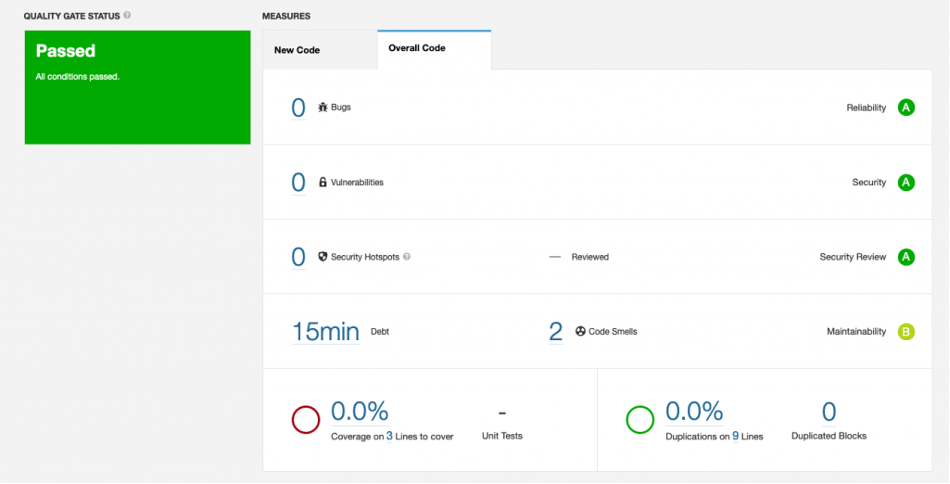
The server created a new project and put the static analysis results in it for you.
Click the project name, and you’ll see a detailed report.
You’ve successfully built a SonarQube server and sent static analysis results to it.
SonarQube Static Analysis
In this post, you learned how to build a SonarQube server and integrate static analysis into a Java build.
SonarQube is a powerful tool that will help you develop better code. You’ve already seen how easy it is to add it to your existing workflow. Learn more about how you can add SonarQube to your development workflow with Cprime’s SonarQube Bootcamp.