Jira Compliance, Part 2: User Management and Auditability
In the previous article, we discussed the importance of considering compliance when configuring an enterprise application ecosystem. Some of the most common compliance standards U.S. companies must consider include the following:
- HIPAA
- SOX
- PCI DSS
- GLBA
- FISMA
- CCPA
- GDPR (if they have customers in the EU)
To comply with these regulations and more, companies need to set up their internal systems properly.
Compliance in Jira
Our focus in this series is on Atlassian Jira. It’s important to know how to optimize Jira and Jira Service Management to support data security and compliance. The four main aspects of compliance in Jira include:
- Approvals – ensuring changes to the system and/or data can only be made by those authorized to do so
- Segregation of Duties – ensuring that no one person can implement a change on their own in Jira without a reviewer
- User Management – maintaining appropriate user permissions and restrictions; knowing who was on-boarded and off-boarded, when, and all the systems that they gained access to in between
- Auditability – the ability to quickly and easily obtain readable exportable reports about activity that took place in Jira
In the first installment of this blog series, we covered Approvals and Segregation of Duties. Here, we will cover User Management and Auditability.
NOTE: Many of the points below touch on the principles of data security. Read our blog series on Atlassian Cloud security.
User Management in Jira
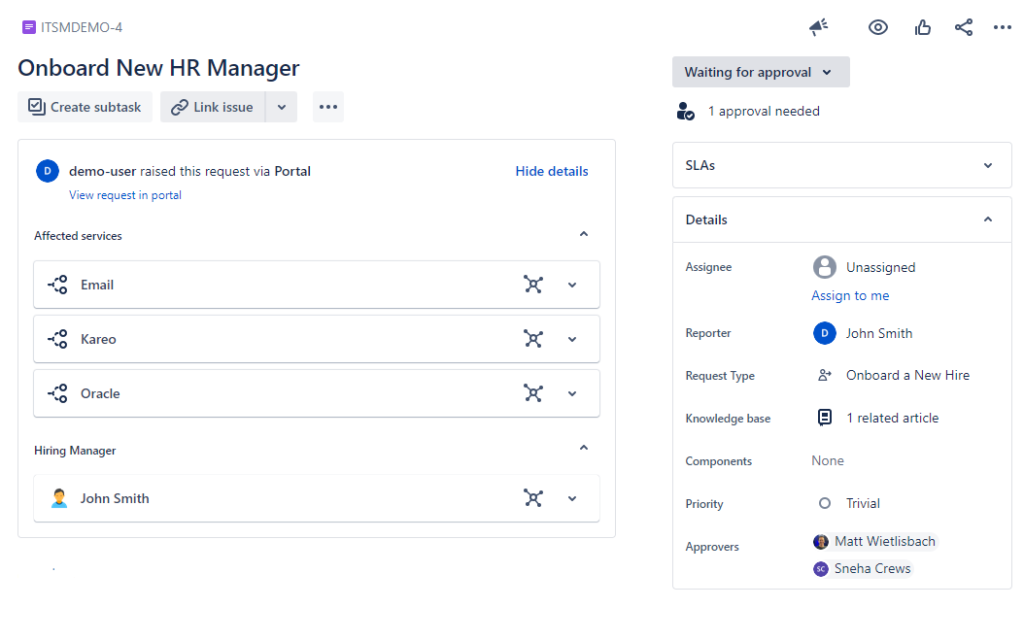
For any compliance standard, user management is key. Importantly, we need to know who was on-boarded and off-boarded, when, and all the systems that they gained access to.
Employee lifecycle management becomes the name of the game when your enterprise needs to meet compliance standards. To clarify, any Identity and Access Management (IAM) system your enterprise uses needs to integrate with your Atlassian suite.
For example, if you’re using Active Directory to manage the user accounts your employees utilize to access your systems, you should tightly integrate Active Directory with Atlassian. If you’re using more cloud-centric IAM systems like Okta, Workday, or other solutions for 2FA or SSO, you should integrate all of these tools with Atlassian.
In the Atlassian Cloud, these integrations will require Atlassian Access. In Jira Data Center, you will not require Atlassian Access but will need to create integrations with all of those tools individually.
With these configurations set up, when your HR systems create a new employee record, the system can automatically create a parallel onboarding request in Jira. And, based on the role, department, or job responsibilities associated with that profile, Jira can detect which systems and services that employee will need access to. You can configure all this business intelligence in the Atlassian tools using Automation Rules and/or scripting plugins like Power Scripts for Jira.
What to do when an employee leaves
Ideally, when an employee undergoes a termination or off-boarding process, admins should already know all the systems they had access to and what access they need to revoke. As a result, administrators should be able to quickly deactivate their access to compliant systems on the day of their departure. It should not take days or weeks to discover the systems they had access to and deactivate their accounts.
Be sure to place special emphasis on those systems containing data that is sensitive under your compliance standard. For example, if you are operating in an ITAR-compliant environment, systems containing government approvals, materials manufacture or regulation data, and any navigation or launch logic should be the highest priority systems to deactivate for that terminated user.
In a PCI or SOX environment, the focus may be on financial management systems, but it’s the same concept. We want to track all systems access for all employees, all the time, to provide a timely deactivation of those systems when the employee leaves.
Keeping all of this Jira data — the associated changes, approvals, custom fields, and issue history — in sync with the individual’s profile in the HR, user management, and IAM systems is key. This allows for a cohesive story that is auditable and automatic across all enterprise applications.
Auditability in Jira
When you configure the previous recommendations (approvals, segregation of duties, and user management) appropriately, auditability is simple. That means:
- Segregation of duties is maintained through custom fields
- Approvals are tracked using Jira Service Management and/or other automation tools
- User management is tightly integrated with your HR tools
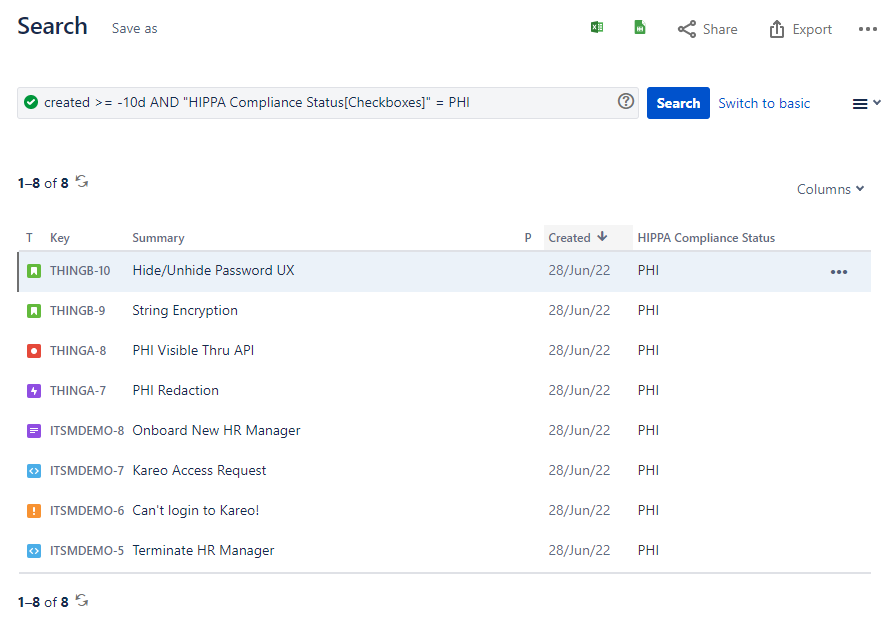
At that point, it becomes seamless, low maintenance, quick, and easy to run a Jira query for system access requests, changes, and development tasks associated with any user, department, role, service, application, or module across any slice of time.
Jira’s out-of-the-box reporting functionality is robust. You can also leverage the power of the Jira Query Language (JQL) to get this information on the fly. These reports are easy to export to CSV, Excel worksheets, and other formats.
If you require live, dynamic dashboards for an Internal Audit group or Compliance Board, you can do this using Jira Dashboards. Or, if you require more visual customization, you can utilize plugins like EazyBI for Jira, or external tools like PowerBI or Tableau.
The power of storing all this information in Jira workflows, custom fields, and issue types is that you can leverage all your normal Business Intelligence tools to get auditability per your compliance standards. You don’t have to implement an expensive new tool to get this information quickly and easily. It’s all right in Jira.
To explore the wider topic of data security in the Atlassian ecosystem, download our whitepaper, Your Quick Hit Guide to Atlassian Cloud Security.